Three days before Substack told users about a security incident, a very different version of the story was already circulating in underground cyber crime forums. On February 2, 2026, a BreachForums user using the alias “w1kkid” claimed to have scraped Substack and extracted close to 700,000 (662,752) user records. By February 5, Substack’s CEO confirmed that user data had been accessed without permission, setting off questions about scale, timing, and what was really taken.
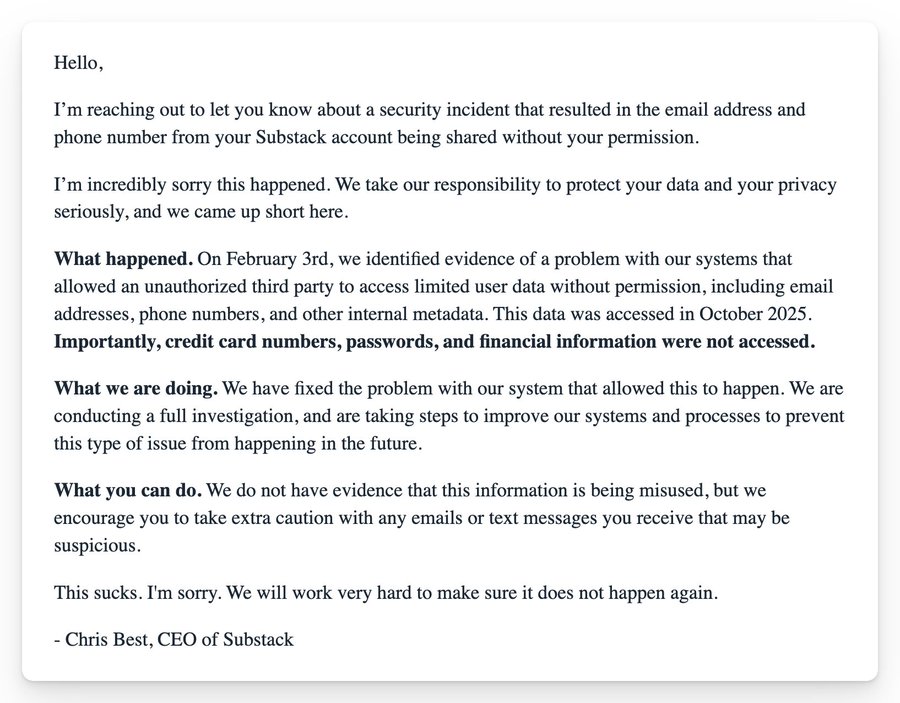
Substack’s notification to users described a system issue that allowed an unauthorized third party to access limited user data. The company said it identified the problem on February 3 and traced the unauthorized access back to October 2025. According to the email, exposed data included email addresses, phone numbers, and internal metadata, while passwords and financial information were not accessed.
What the Exposed Substack Data Shows
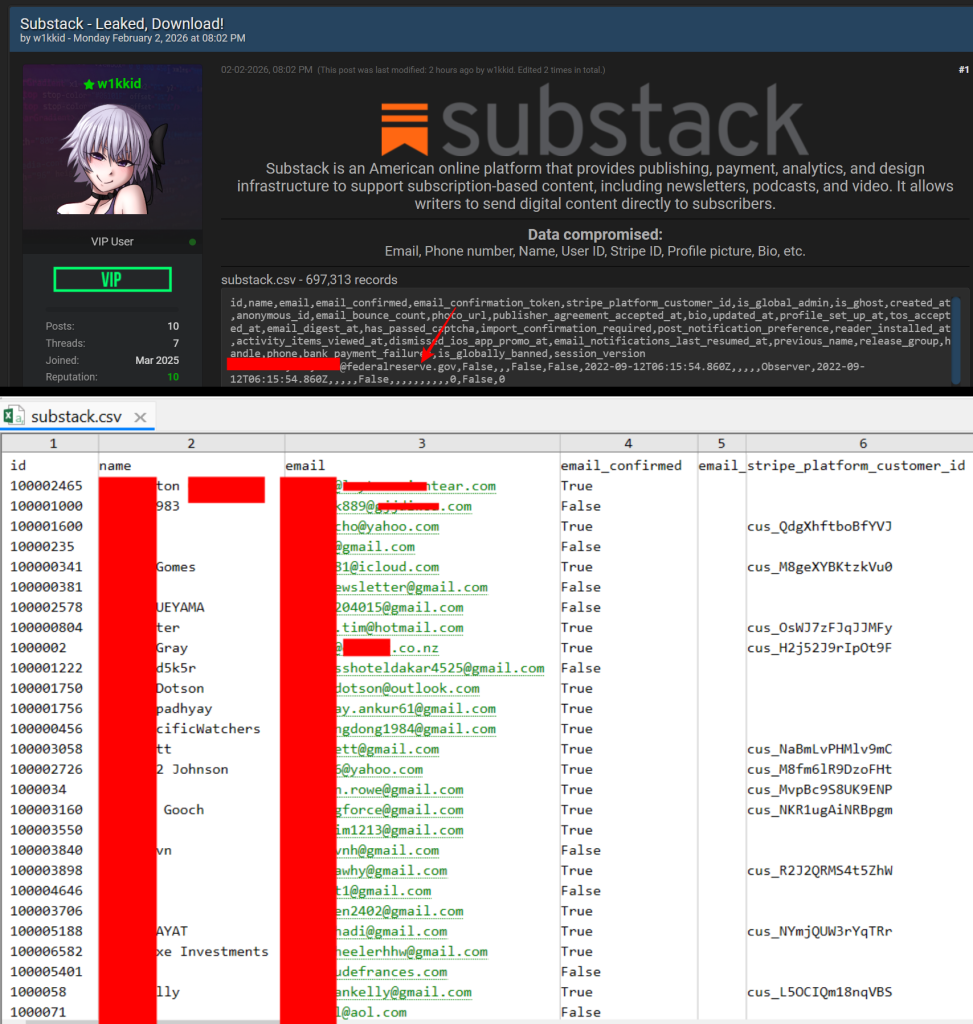
However, the data shared on BreachForums shows a more detailed picture of what that access may have looked like. Sample rows show what appear to be complete user account records, each linked to a unique numeric ID and account creation dates, update timestamps, notification preferences, and moderation flags. These are not the kinds of fields visible on public profile pages.
After indepth analyssi of the entire database Hackread found that several records belong to active publishers rather than passive readers. Publisher agreement acceptance timestamps appear in the data, along with newsletter handles, biographies, and profile images hosted on Substack’s own S3 buckets. This indicates that creator accounts, including those linked to monetized publications, were part of the exposed dataset.
Stripe platform customer IDs appear across multiple entries. While these identifiers do not expose payment card details, they directly link Substack accounts to Stripe customer objects. From a security perspective, that connection increases the sensitivity of the data because it allows correlation between identity information and payment systems.
Phone numbers are also present for users in multiple countries, alongside verified email addresses and long account histories. Some accounts date back to 2018, while others show updates as late as 2025. This mix suggests a broad snapshot of user data rather than selective collection of recent or public profiles.
The internal nature of the fields included is difficult to reconcile with a simple scrape. Flags such as is_global_admin, is_ghost, is_globally_banned, session_version, and has_passed_captcha are backend indicators used by the platform itself. Their presence suggests access to internal systems or data exports rather than harvesting through public interfaces.
No Evidence of Data Abuse So Far?
Substack said it has no evidence that the data is being misused and that it has fixed the underlying issue. In breach investigations, that usually means no confirmed abuse has been detected yet. Datasets of this type often circulate privately before being used for phishing, impersonation, or targeted social engineering. Hackread.com can confirm that this specific Substack is now circulating on several Russian speaking cyber crime forum as we well exchanged on Telegram.
For impacted users, the main risk now is targeted phishing. Emails or text messages may arrive that reference your Substack account, newsletter name, bio, or signup history to appear legitimate. Do not click links, download attachments, or respond to messages claiming to be from Substack, Stripe, or subscribers asking for verification or payment details.
Access your account only by typing the official site address directly into your browser, and ignore messages that create urgency or request one-time codes, password resets, or account confirmation. If you use the same email or phone number on other services, watch for similar messages there as well.