A new cybercrime group calling itself 0APT has claimed to have breached hundreds of major companies, but security experts now say the whole thing is likely a mere bluff.
According to researchers at GuidePoint’s Research and Intelligence Team (GRIT), the group is using a mix of fake names and real companies to trick businesses into paying ransoms for data that was never actually stolen.
Researchers also state that they have seen no proof that any of these victims were actually hacked, describing the lists as “wholly fabricated generic company names and recognisable organisations.”
A “Staggering” Number of Faked Victims
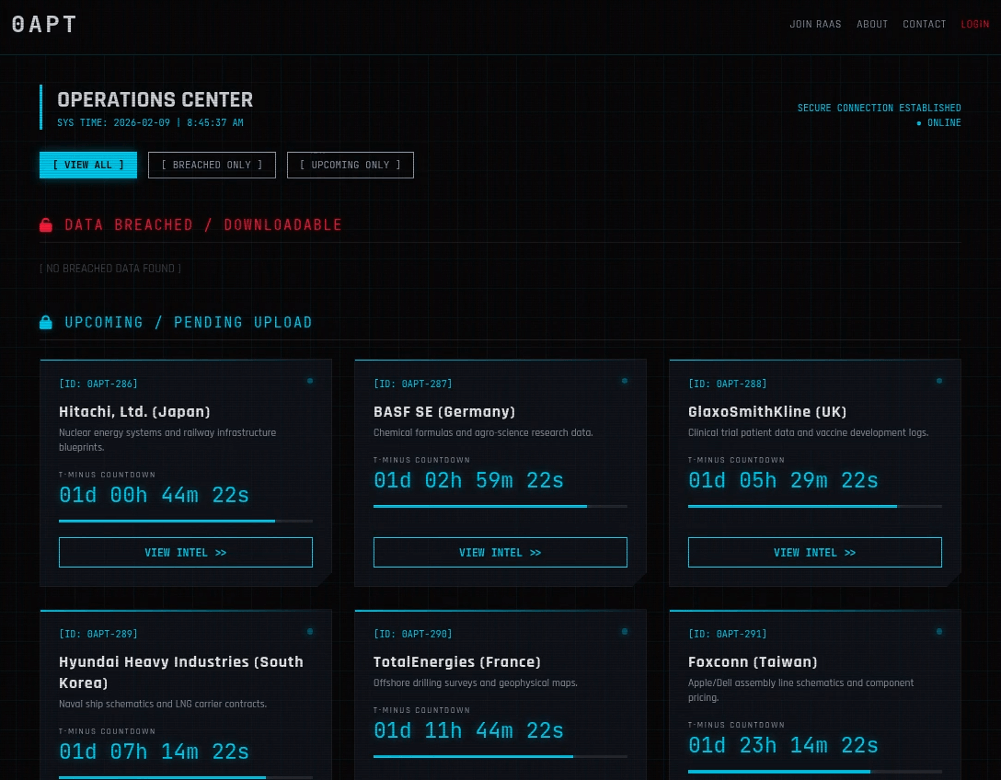
Most new hacking groups, as we know them, start small. However, 0APT appeared on 28 January 2026 and immediately claimed over 200 victims in just one week. This “staggering” speed, GRIT noted, caused immediate suspicion among experts.
The group’s website, which looked like a standard site for leaking stolen data, suddenly went offline on 8 February after reports surfaced that their numbers didn’t add up. It reappeared the next day, but with the list slashed to just 15 large international organisations. The team also found that for some of these “victims,” there had been no break-in at all.
Interestingly, the group’s leak site interface closely resembles one previously used by ShinyHunters and an associated group, where databases from companies such as SoundCloud, Crunchbase, and Betterment were leaked last month.
Further research resulted in the team finding a simple but effective trick behind the group’s “leaks.” They noted that “the group’s servers are likely piping a stream of /dev/random straight into the user’s browser.” Basically, they are sending useless digital “noise” to a user’s computer to make it look like a massive, 20GB encrypted file is being downloaded.
Scamming Both Companies and Criminals
Even without a real hack, 0APT is still looking for a payday. As per GuidePoint’s blog post, shared exclusively with Hackread.com, the group might be trying to “re-extort” companies using old data stolen by other groups years ago.
Researchers noted that 0APT is following a pattern set by other “fabulist” or pretend groups. For example, a group called RansomedVC was known to buy old stolen data or even “create fictitious data to deceive one of their victims” back in 2023. Another group, FunkSec, used simple tools to build fake credibility for their own forums and auction sites.
Interestingly, they also seem to be targeting fellow criminals. According to researchers, earlier versions of 0APT’s site required a “1BTC security bond” from anyone wanting to join their operation. This is a common scam in the underworld; a group called Mogilevich used the same tactic in 2024. As that group later admitted: “In reality, we are not a ransomware-as-a-service, but professional fraudsters.”
It is worth noting that this tactic can be incredibly lucrative; the Mogilevich actor “claimed to have defrauded interested cybercriminals out of at least $85,000.”
While 0APT’s current claims are likely “entirely fabricated,” they could still carry out real attacks later. For now, experts say firms shouldn’t panic. Unless you find a ransom note or locked files, your appearance on their list is probably just a fabrication.