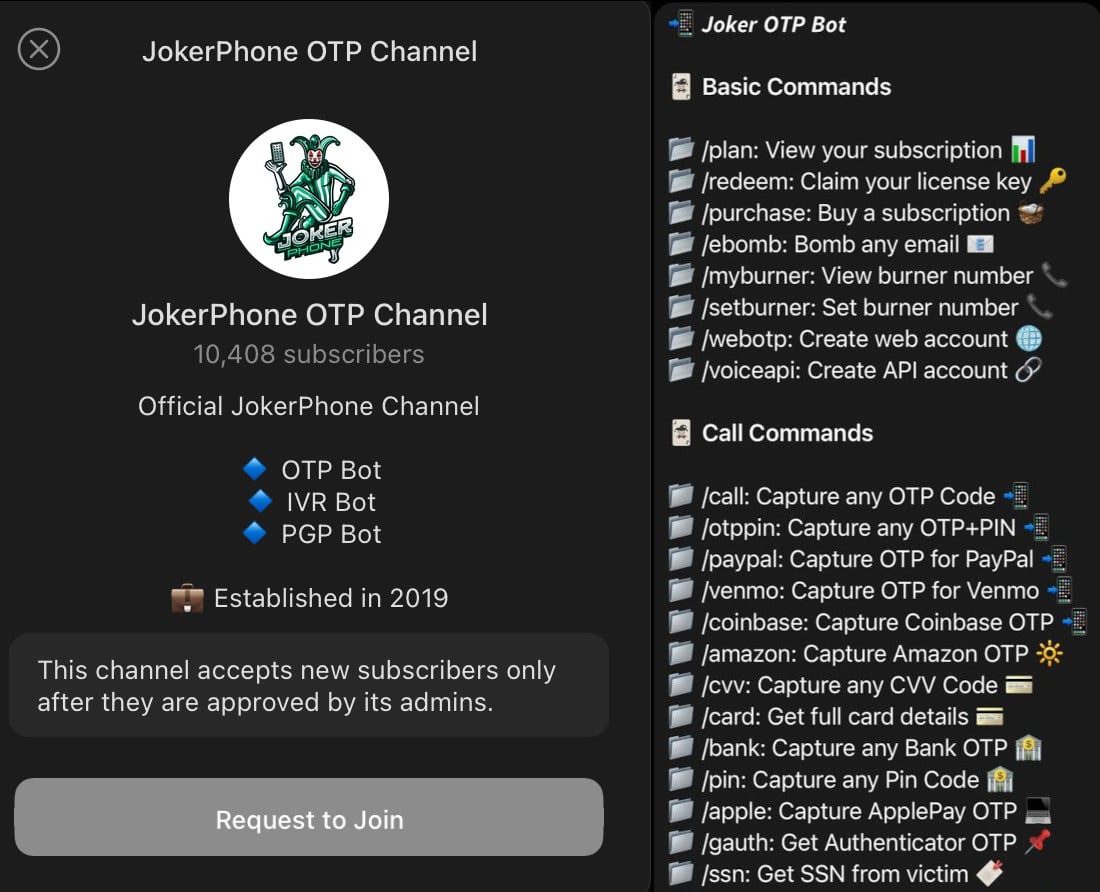
The Netherlands Police have arrested a a 21-year-old man from Dordrecht, suspected of selling access to the JokerOTP phishing automation tool that can intercept one-time passwords (OTP) for hijacking accounts.
The suspect is the third one arrested after authorities after a three-year investigation that led to dismantling the JokerOTP phishing-as-a-service (PhaaS) operation in April 2025.
At the time, authorities arrested the developer of the platform, and in August, a co-developer who used the aliases ‘spit’ and ‘defone123’.
In two years, the JokerOTP malicious service allegedly caused at least $10 million in financial losses in more than 28,000 attacks targeting users in 13 countries.
The seller, whose name has not been disclosed, used a Telegram account to advertise access to the phishing platform via license keys.
Cybercriminals subscribed to the service could configure the tool to automate calls to victims and capture temporary codes or other sensitive data (PIN codes, card data, social security numbers).
The JokerOTP bot could target users of PayPal, Venmo, Coinbase, Amazon, and Apple.
OTPs are temporary codes serving as an additional security layer in account authentication. They can be sent via SMS or email, or generated by a specialized application, when users try to log into an account.
These codes have short expiration times and are meant to ensure that access to an account is reserved only to the rightful owner, blocking fraudulent attempts from actors who might have stolen or guessed (brute-forced) the credentials.
Typically, cybercriminals would use stolen credentials, either collected from malware infections or purchased on the dark web, and try to log into a target account. The legitimate owner would receive the OTP required for completing the login process.
At the same time, JokerOTP automated calls to targets, posing as representatives of the legitimate service the attackers were attempting to access, and requesting the one-time password (OTP).
Because the calls coincided with the delivery of the authentication code, many users failed to recognize the scam.
“Victims were automatically called by the bot and informed that criminals were attempting to gain access to their account,” explained Anouk Bonekamp, team leader of Cybercrime Oost-Brabant.
“The bot then asked them to enter the one-time password. Victims, therefore believe they are protecting themselves by cooperating and providing information.”
Depending on the type of compromised account, threat actors may use their access to make unauthorized purchases, transfer funds to bank accounts they control, or hijack the account.
The police say the investigation is still underway, and dozens of JokerOTP bot buyers in the Netherlands have already been identified and will be prosecuted in due time.
Bonekamp further commented that victims of such scams should not feel ashamed for falling for the sophisticated trap and should stay alert for signs of fraud, such as the creation of urgency and requests to disclose sensitive info like PINs and passwords.
The police also suggest that users check for data breaches impacting them on the Have I Been Pwned and Netherland Politie’s CheckJack services, as the leak of emails and other sensitive data significantly increases the risk of being targeted by tools like JokerOTP.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
Related Articles:
Spain arrests 34 suspects linked to Black Axe cyber crime
Black Basta boss makes it onto Interpol’s ‘Red Notice’ list
Hacker gets seven years for breaching Rotterdam and Antwerp ports
Former Coinbase support agent arrested for helping hackers
Hacker arrested for KMSAuto malware campaign with 2.8 million downloads