A newly identified cyber espionage group has been targeting government and telecommunications organizations across Africa, the Middle East and Asia for at least the past two and a half years, according to Palo Alto Networks.
The group was tracked as activity cluster CL-STA-0043 by Palo Alto’s Unit 42 research team in 2022 and 2023.
In 2024, it was allocated its own temporary group classification, TGR-STA-0043, and campaign codename, Operation Diplomatic Specter.
In a new report, published on September 30, 2025, Unit 42 researchers elevated TGR-STA-00043 to a distinct threat group under the name Phantom Taurus.
As part of its cyber-espionage campaigns, the group has targeted ministries of foreign affairs, embassies, geopolitical events and military operations. Its activity aligns with Chinese state interests.
Phantom Taurus: Targeting and Attack Techniques
According to the Unit 42 report, Phantom Taurus typically conducts long-term intelligence collection operations against high-value targets to obtain sensitive, non-public information.
The group takes a specific interest in diplomatic communications, defense-related intelligence and the operations of critical governmental ministries, with campaigns that frequently coincide with major global events and regional security affairs.
While Phantom Taurus previously focused on exfiltrating sensitive emails from compromised email servers, the group has recently pivoted to directly targeting SQL Server databases for data theft.
The group’s operations now involve a custom batch script (mssq.bat), which they execute remotely via Windows Management Instrumentation (WMI) to query and extract information from databases.
The script operates as follows:
- Authenticating to the SQL Server using the system administrator account and a pre-compromised password
- Dynamically executing queries supplied by the operators (e.g., searching for tables/keywords related to specific countries like Afghanistan and Pakistan)
- Exporting results to CSV files for exfiltration before closing the connection
This tactical shift suggests an expanded focus on structured data repositories, likely to harvest intelligence or sensitive documents more efficiently than email-based theft alone.
Using WMI for remote execution further highlights the group’s reliance on living-off-the-land (LotL) techniques to evade detection.
Phantom Taurus uses an operational infrastructure that has exclusively been used by Chinese threat actors, including Iron Taurus (aka APT27), Starchy Taurus and Stately Taurus (aka Mustang Panda).
However, the specific infrastructure components used by Phantom Taurus have not been observed in operations by other threat actors, indicating operational compartmentalization within this shared ecosystem.
Additionally, Phantom Taurus uses a unique set of techniques, tactics and procedures (TTPs), that makes it stand out from other groups.
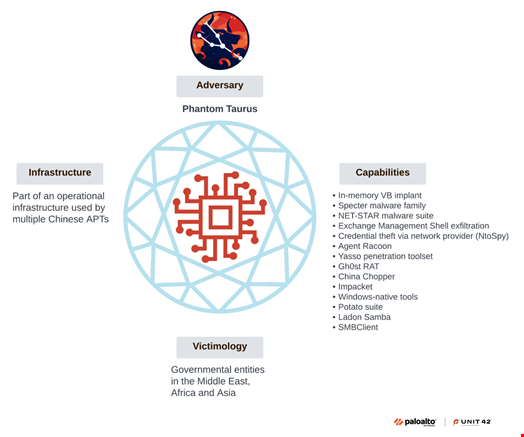
Alongside common tools such as China Chopper, the Potato suite and Impacket, the group uses some tools and techniques that have never been observed in operations by other groups and others that have very rarely been used by other threat actors.
These include the Specter malware family, Ntospy and NET-STAR, a newly identified malware suite.
NET-STAR, A New Custom-Made Malware Suite
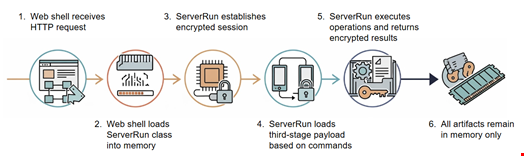
The Unit 42 report shared findings on an undocumented .NET malware suite deployed by Phantom Taurus to target Internet Information Services (IIS) web servers.
This newly identified tool, dubbed NET-STAR by the security researchers based on the use of the string in the malware’s program database (PDB) paths, “demonstrates Phantom Taurus’ advanced evasion techniques and a deep understanding of .NET architecture,” noted the Unit 42 report.
The suite comprises three distinct web-based backdoors, each serving a specific role in the attack chain while maintaining persistence within the target’s IIS environment:
- IIServerCore: a fileless modular backdoor that supports in-memory execution of command-line arguments, arbitrary commands and payloads
- AssemblyExecuter V1: an older version of custom-made .NET assembly designed for a single, specific purpose of executing other .NET assemblies directly in memory without writing them to disk (used by Phantom Taurus in 2024 campaigns)
- AssemblyExecuter V2: a new, enhanced version of AssemblyExecuter V1 equipped with Antimalware Scan Interface (AMSI) and Event Tracing for Windows (ETW) bypass capabilities (used by Phantom Taurus since early 2025)
Read more: Chinese Cyber Espionage Campaign Impersonates US Congressman