Thousands of organizations could be vulnerable to attack after researchers discovered four critical vulnerabilities in the products of Axis Communications, a leading manufacturer of CCTV cameras and surveillance equipment.
OT security firm Claroty and its research branch, Team82, shared findings at Black Hat USA, in Las Vegas, on August 6.
Flaws in Axis Proprietary Client-Server Communication Protocol
Team82 researcher, Noam Moshe, discovered the vulnerabilities which all originating from a fundamental flaw in Axis.Remoting, a proprietary communication protocol used between client applications and Axis’ servers.
Upon discovery, Team82 quickly notified Axis Communications, which publicly reported them – the manufacturer is a certified Common Vulnerabilities and Exposures (CVE) Numbering Authority (CNA).
They are tracked as follows:
- CVE-2025-30023. A critical flaw (CVSS score: 9) affecting Axis Camera Station Pro before version 6.9, Axis Camera Station before version 5.58 and Axis Device Manager before version 5.32 that could lead to an authenticated user performing a remote code execution (RCE) attack
- CVE-2025-30024. A medium-severity flaw (CVSS score: 6.8) affecting Axis Device Manager before version 5.32 that could be leveraged to execute a man-in-the-middle (MitM) attack
- CVE-2025-30025. A medium severity flaw (CVSS score: 4.8) affecting Axis Camera Station version 5, Axis Camera Station Pro before version 6.7 and Axis Device Manager before version 5.32 that could lead to a local privilege escalation
- CVE-2025-30026. A medium severity flaw (CVSS score: 5.3) affecting Axis Camera Station before version 5.58 and Axis Camera Station Pro before version 6.9 that could allow an authentication bypass attack
The manufacturer stated in its advisories that it had observed no in the exploitation in the wild of any of the four flaws.
It also released patches in the following software updates:
- Axis Camera Station Pro 6.9
- Axis Camera Station 5.58
- Axis Device Manager 5.32
Despite public disclosure, the CVE entries still currently appear under the ‘Reserved’ status on the website of the CVE program, suggesting that more information will be made available after the Team82 session at Black Hat, which is to be held on August 6.
On the US National Vulnerability Database (NVD) website, the four vulnerabilities are registered under the status ‘Awaiting Analysis,’ which typically means that the NVD team has not yet added any enriched data around these flaws.
6,500 Axis Communications Servers Exposed
Despite no known records of exploitation, the Team82 researchers discovered more than 6,500 servers exposing this protocol and its services to the internet, more than half of those (almost 4,000) in the US. This came following an internet scan using tools like Censys and Shodan.
“Each of these servers could potentially manage hundreds or thousands of individual cameras. Given current bans on Chinese technology in many corners of the world, an organization’s choice of vendors has become somewhat limited, putting more emphasis on the protection of platforms available for these deployments,” the researchers added.
Team82 developed an exploit chain that targets vulnerabilities in the Axis.Remoting communication protocol.
According to their findings, the attack enables unauthorized access to both the centralized Axis Device Manager and the Axis Camera Station.
Successful exploitation of these vulnerabilities could allow an attacker to infiltrate an internal network and execute code remotely on either the server or client systems.
Additionally, Team82 highlighted that an attacker positioned as a MitM could exploit a pass-the-request flaw in the protocol, potentially decrypting traffic and achieving remote code execution.
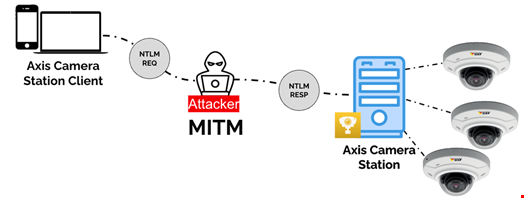
They also warned that by scanning the internet for exposed Axis.Remoting services, an attacker could identify vulnerable servers and clients, facilitating precise and targeted attacks.
“Team 82 wishes to acknowledge Axis Communications’ quick response to our disclosure. They accepted our disclosure report and worked on the patches and updates in a timely fashion,” read the report.
Photo credits: Fredrik Eriksson / ChristianLphoto / Shutterstock.com