
Automated Incident Response: Everything You Need to Know

Katie Bykowski
Automated Incident Response: How It Works & Expert Tips
Automated incident response streamlines how security teams detect, investigate, and remediate threats by using predefined workflows and machine-driven actions. Instead of relying solely on manual intervention, automation helps respond to incidents faster, reduce errors, and maintain consistency across your security operations.
In this article, we’ll break down how automated incident response works, why it’s essential for today’s threat landscape, and share expert tips to help you implement it successfully.
Cybersecurity management is increasingly challenging. Many organizations face a surge in threats without enough staff or resources to keep up, leaving up to 68% of critical vulnerabilities unresolved. With large enterprises processing over 10,000 alerts daily, each potentially taking 10 to 40 minutes to investigate, security teams quickly become overwhelmed. Manual workflows and inconsistent triage methods further slow response times, fail to integrate available tools, and risk losing critical knowledge to staff turnover, all while compliance demands keep evolving.
That’s why automated incident response has become essential. By streamlining how alerts are detected, investigated, and resolved, automation helps security teams overcome these inefficiencies, reduce risk, and maintain a resilient security posture.
What is Automated Incident Response?
Automated incident response uses automation to monitor security alerts and automatically respond with pre-defined IR processes from your incident response plan, which allows SOC analysts to focus on strategic and proactive threat hunting.
It is a popular solution for dealing with the overwhelming number of security threats your organization faces. With automated incident response, alert monitoring is streamlined and response times significantly decrease. Cyber incident response automation allows you to address every alert and reduce risk exposure.
Automating your response to security threats enables your security operations team to triage alarms more effectively, respond to critical events faster, and seamlessly integrate your existing security solutions into a more efficient and comprehensive incident response program.
How Does Incident Response Automation Work?
An automated incident response solution provides your organization with the tools to model and automates many of your manual and labor-intensive response processes.
Tasks that can be automated include:
- Reviewing and analyzing threat intelligence sources
- Investigating incidences involving log gathering and analysis
- Updating tickets
- Gathering metrics and creating reports
- Sending email alerts
- Resolving alerts
With every automation, security teams can save precious minutes on each alert, which quickly accumulates into hours of saved work and improved security incident response.
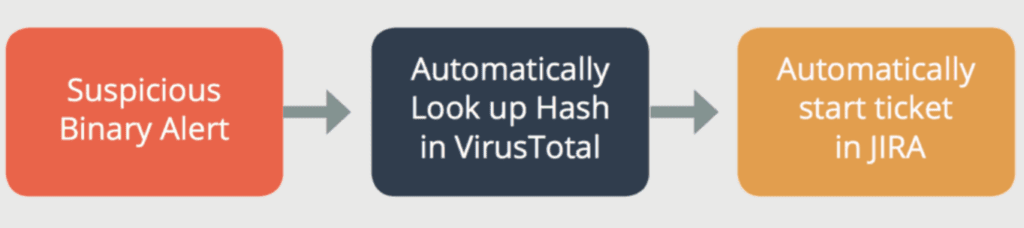
Automating Incident Management Process
Automating the incident management process means using technology to handle the key stages of threat detection and response with minimal manual intervention. Here’s how it typically works:
- Detection: Automation ingests and monitors data from various sources—like SIEMs, EDRs, firewalls, and cloud environments—to identify suspicious activity or anomalies in real time.
- Triage & Enrichment: When a potential incident is detected, automated workflows enrich the alert by pulling in context—such as asset details, threat intelligence, or user behavior—to assess its severity and relevance.
- Decision & Prioritization: Rules or machine learning models evaluate the enriched data to decide if the incident meets the threshold for further action, helping prioritize critical threats over low-risk noise.
- Response: Predefined playbooks automatically execute containment or remediation actions, such as isolating a device, blocking an IP, or disabling a compromised account.
- Notification & Escalation: If needed, the system escalates incidents to human analysts for deeper investigation, while automatically documenting actions taken.
- Post-Incident Analysis: The process closes the loop by logging all activities, generating reports, and updating case management systems to support audits and continuous improvement.
Incident Response Automation Tools
Incident response automation tools enable security teams to efficiently detect, analyze, and respond to threats by orchestrating workflows that would otherwise demand countless hours of manual effort. Unlike traditional SOAR platforms, advanced solutions like Swimlane Turbine leverage AI-driven automation to process vast streams of security telemetry, enrich data in real time, and execute incident response with speed and precision.
Here’s how these tools typically work:
- Automated Ingestion & Analysis: Continuously pull in data from your SIEM, EDR, cloud workloads, and threat intelligence feeds to identify and prioritize suspicious activity.
- AI-Powered Playbooks: Use intelligent automation to investigate incidents, apply business logic, and execute response actions — such as isolating endpoints, disabling user accounts, or blocking malicious IPs — all without human delays.
- Contextual Enrichment: Automatically layer in asset details, user context, and threat intel to give each alert meaning, reducing false positives and improving decision-making.
- Centralized Case Management: Maintain a single system of record for incident tracking, evidence, and audit trails, streamlining investigations and compliance reporting.
- Scalable, Resilient Architecture: Handle millions of daily events and automate processes both inside and beyond the SOC, reducing manual workloads and analyst fatigue.
Benefits of Automating Incident Response
Incident response automation allows your organization to handle more threats without increasing workload or headcount. Other top benefits of incident response automation include:
1. Get Critical Event Context and Insights in Real Time.
Address risk management planning and future security needs with real-time insights into incidents. You can gain a deep understanding of your organization’s current security posture with the help of intuitive dashboards. These also make it easier to provide reporting for security audits and compliance as well.
2. Gain Visibility into Your Technology Stack.
Some incident response platforms offer the ability to integrate with anything, This allows your SOC analysts to pull data into a single case management platform, instead of bouncing between tools to find threats.
3. Improve SOC Analyst Job Satisfaction
Automated incident response processes take manual work off the shoulders of SOC analysts, which saves them time and reduces burnout. In turn, analysts can focus on training, skill-building and triaging strategically. This force multiplier has the additional positive effect of increasing morale and lowering staff turnover as the tedium and stress of the workday is reduced.
4. Improve Security Performance Metrics
Automation allows you to consistently respond to security alerts and enable your incident response team to analyze and remediate more threats. It makes your security operations more efficient, improves mean-time-to-resolution (MTTR) and automatically quantifies ROI by reporting on incident response metrics in a unified dashboard.
What to Look for in an Automated Incident Response Solution
Not all automated incident response solutions are built the same. Core capabilities and features to look for include:
- Approachable Automation: You’ll gain the most value from incident response software that makes automation simple. Make sure the solution offers easy-to-build, modular playbooks that the whole team can utilize.
- Endless Integration Capabilities: Look for an extensive library of out-of-the-box integrations, as well as the option to integrate with anything.
- Dynamic Case Management: Case managements helps to speed up investigations, ensure compliance processes and make it easy to resolve more security alerts.
- Intuitive Dashboards: Seek out a solution that offers customized dashboards designed to fit any use case. You’ll see exactly how your IR processes are functioning with detailed analyst views and macro-level management dashboards.
- Customized Incident Reports: Reporting capabilities help your team quickly pull relevant data into high-level visual insights and in-depth reports.
Incident Response with AI Automation
AI security automation, like the Swimlane Turbine platform, replaces your organization’s manual and time-consuming incident response methods with a centralized automated system.
With low-code security automation, you can:
- Track enterprise security tasks automatically
- Centralize data into accessible reports, dashboards and metrics
- Standardize the threat response and notification processes
- Leverage endless APIs to rapidly respond and prevent attacks sooner
Watch how your team can use Swimlane to automate incident response processes.
TL;DR: Automated Incident Response
TL;DR: Automated Incident Response: Automated incident response has become increasingly necessary as today’s threat landscape continues to grow. When it’s time to select a solution, look for one that can adapt to your organization’s future security needs, on top of providing immediate support. Cyber threats are here to stay, so make sure your automated incident response tool can stand the test of time.

A Buyer’s Guide for Modern Security Automation
Enterprise SOC teams recognize the need for automation but often struggle with the automation solutions themselves. Security Orchestration, Automation and Response (SOAR) solutions commonly require extensive scripting. No-code automation solutions are simplistic and lack necessary case management and reporting capabilities. This guide analyzes the wide range of security automation platforms available today, so you can identify the type of solution that fits your needs the best.
Tags
Request a Live Demo
The post Automated Incident Response: Everything You Need to Know appeared first on AI Security Automation.
*** This is a Security Bloggers Network syndicated blog from Blog Archives - AI Security Automation authored by Katie Bykowski. Read the original post at: https://swimlane.com/blog/automated-incident-response/
