A new Atomic macOS Stealer (AMOS) campaign is targeting macOS users by disguising the malware as “cracked” versions of legitimate apps, Trend Micro researchers have warned.
The campaign is designed to help cybercriminals overcome recent Apple security improvements, representing “significant tactical adaptation,” the researchers found.
“While macOS Sequoia's enhanced Gatekeeper protections successfully blocked traditional .dmg-based infections, threat actors quickly pivoted to terminal-based installation methods that proved more effective in bypassing security controls,” they noted.
Victims are lured into installing the infostealer via social engineering techniques – either downloading a malicious .dmg installer masquerading as a cracked app or, after being asked to copy and paste commands into the macOS terminal, resembling the fake CAPTCHA technique.
Once installed, AMOS establishes persistence before stealing sensitive data from the victim’s system. This includes credentials, browser data, cryptocurrency wallets, Telegram chats, VPN profiles, keychain items, Apple Notes and files from common folders.
AMOS’ Infection Chain and Delivery
The Trend Micro report, published on September 4, observed that the attackers attempt to gain initial access to systems through cracked software downloads.
Affected users visited the website haxmac[.]cc several times. This URL hosts several cracked software programs for macOS.
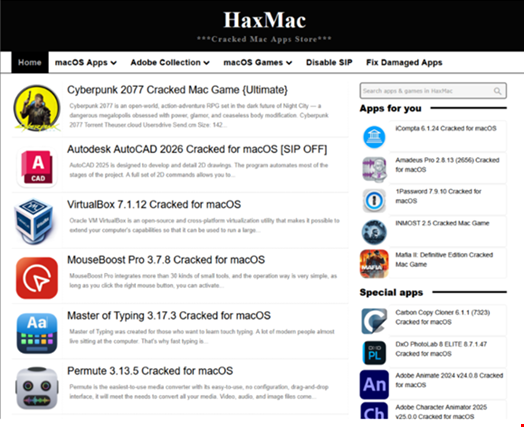
In the cases analyzed, the users specifically searched for and downloaded “CleanMyMac” on their machines. This is a legitimate program that can be downloaded from the Mac App Store.
“However, downloading the program from an untrusted source, as seen in these cases, puts the machine and the organization at risk because these cracked programs might be bundled with malware or trojanized by threat actors,” the researchers noted.
After downloading the cracked software, victims are redirected to AMOS’ landing page, prompting them to click “Download for MacOS” or instructed to copy and paste malicious commands into the Apple Terminal.
This page appears to perform OS fingerprinting, determining whether the visitor is using Windows or MacOS before redirecting them to the corresponding payload page.
A number of different domains were observed to act as redirectors, while the redirect destination changes with each visit to help bypass detection. However, the instructions on the pages remain identical.
Additionally, the threat actor uses frequent domain and URL rotation for their download commands, likely to evade static URL-based detections and takedowns.
“As a result, the domains and URLs are expected to change over time,” the researchers said.
Both of these actions lead to the execution of a malicious installation script. This script downloads an AppleScript file “update” to the temp directory.
A script ‘com.finder.helper.plist’ file configures a MacOS LaunchDaemon to continuously run the ‘. agent’ script, which then runs in an infinite loop to detect the logged-in user and execute the hidden binary.
The binary file establishes persistence by retrieving the username of the currently logged-in user, excluding root.
Once the script is executed, it copies sensitive data from the compromised system.
The researchers said that the type of information stolen by AMOS poses significant downstream risks for businesses as well as the individuals targeted. This includes credential stuffing, financial theft or further intrusions into enterprise systems.
The researchers urged organizations to deploy defense-in-depth strategies that don’t rely solely on built-in operating system protections to protect against the tactics used in this campaign.
Image credit: IgorGolovniov / Shutterstock.com