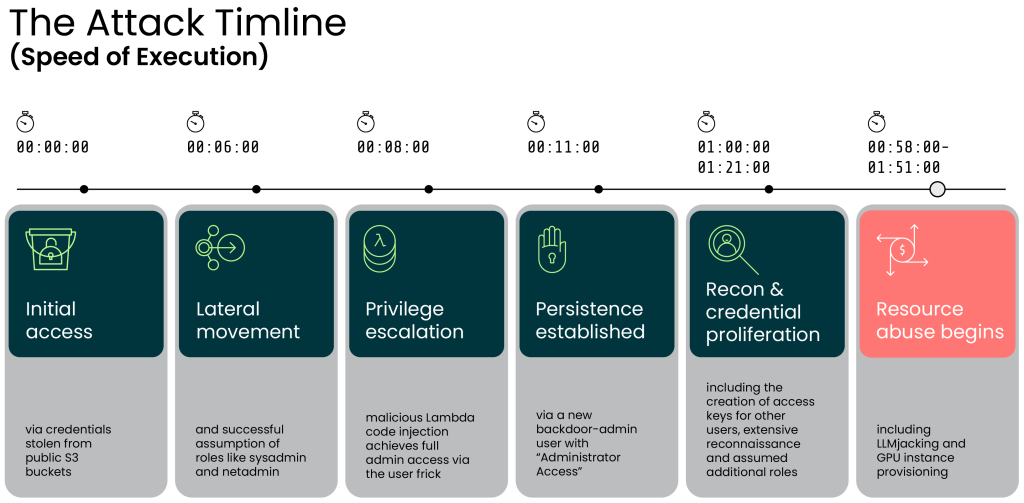
On 28 November 2025, experts from the Sysdig Threat Research Team (TRT) watched an attacker take over a company’s cloud environment in record time. While we usually think of cyber attacks as slow, systematic processes, this person managed to gain total control in just eight minutes.
The Break-In
It all started with a simple mistake. The hacker found test credentials left in a public digital storage area, known as an S3 bucket. These buckets act like online folders, but this one was accidentally left open. Researchers noted that the buckets even had AI in their names, making them easy targets for anyone searching for data to steal.
Interestingly, the stolen account already had a ReadOnlyAccess policy, which the hackers used to conduct a massive scouting mission across the victim’s entire system, from databases to security keys. They looked into services like Secrets Manager, RDS, and CloudWatch to map out the environment before making their move.
Next, they used a clever trick called code injection to target Lambda functions (small bits of code that run tasks automatically) and obtain higher levels of authority. Further probing revealed that the intruder repeatedly edited a function named EC2-init until they successfully hijacked an account named ‘frick’, which gave them full administrative powers.
A New Kind of Threat
This wasn’t just a fast human at a keyboard. According to Sysdig’s investigation, the speed and style of the code suggest that the hacker used Large Language Models (LLMs) to automate the work. Interestingly, the code contained notes written in Serbian, and it was typed so quickly that a human might not have been able to type it manually.
The attack didn’t stop at just stealing data. The hacker engaged in LLMjacking, where they used the victim’s account to run expensive AI models like Claude 3.5 Sonnet, DeepSeek R1, and Amazon Titan.
They even tried to launch a massive computer they called the stevan-gpu-monster to train their own AI. If they hadn’t been stopped, that one machine would have cost the company over £18,000 ($23,600) every month.
Hiding in Plain Sight
The attackers were good at staying hidden, using an IP rotator to constantly change their digital address, and moved through 19 different identities to blend in. The compromised account was actually a “child account” inside a larger organisation, and the hacker tried to “jump” into other accounts by guessing a default role called the OrganizationAccountAccessRole.
Furthermore, researchers found AI hallucinations in the attack, which means the hacker’s script tried to connect to fake AWS account IDs like “123456789012,” a common mistake AI makes when it tries to fill in blanks.
“This attack stands out for its speed, effectiveness, and strong indicators of AI-assisted execution. The threat actor achieved administrative privileges in under 10 minutes, compromised 19 distinct AWS principals, and abused both Bedrock models and GPU compute resources. The LLM-generated code with Serbian comments, hallucinated AWS account IDs, and non-existent GitHub repository references all point to AI-assisted offensive operations,” researchers explained.
To prevent this, the Sysdig team says companies must stop leaving access keys in public areas and should use “IAM roles,” which provide temporary access instead. Watching for massive enumeration, where a user suddenly tries to list every single file in an account, is one of the best ways to catch these hackers before they finish.
Expert Analysis:
In comments shared exclusively with Hackread.com, industry leaders weighed in on the significance of this high-speed breach.
“The cybersecurity world today is brand new,” said Ram Varadarajan, CEO at Acalvio. He explained that in this threat environment, “organizations have to accept that the speed of the breach has shifted from days to minutes.” Varadarajan added that to stay ahead, teams need to deploy “cyber defenses that are AI-aware” to catch these machines at their own speed.
Shane Barney, Chief Information Security Officer at Keeper Security, pointed out that the failure was structural rather than a new “clever exploit.” He noted that “AI doesn’t invent new attack vectors here. It removes hesitation.” According to Barney, the most concerning part was how “quietly” the attack happened because “identity and privilege boundaries were too loose.” He urged companies to treat automated accounts with the “same rigor as human administrators.”
Jason Soroko, Senior Fellow at Sectigo, highlighted that while AI played a role, a “mundane error” was the true culprit. “The entire compromise began because the victim left valid credentials exposed in public S3 buckets,” Soroko said. He warned that “It is impossible to defend a cloud environment when the keys are left visible to anyone who bothers to look.