Disclosure: This article was provided by ANY.RUN. The information and analysis presented are based on their research and findings.
ANY.RUN experts are observing a new wave of phishing campaigns that abuse trusted cloud and CDN infrastructure, including platforms run by Google, Microsoft, and Cloudflare, as active hosting environments, not just delivery layers.
What’s changing isn’t the technique itself, but how consistently and deliberately it’s now used to bypass enterprise security controls. By hiding phishing kits inside legitimate cloud services and filtering victims to target corporate accounts, attackers reduce early detection and increase the chance of business-impacting outcomes such as account takeover, invoice fraud, and internal spread.
Why Trusted Cloud Hosting Changes the Detection Game
For years, phishing detection relied heavily on spotting weak signals: newly registered domains, suspicious hosting providers, or short-lived infrastructure. That model starts to break down when phishing kits are hosted on legitimate cloud and CDN platforms operated by companies like Google, Microsoft, and Cloudflare.
From a network and email security perspective, these campaigns often look indistinguishable from normal business traffic. URLs resolve to trusted providers, TLS certificates are valid, and content is delivered as standard HTML from well-known cloud endpoints. As a result, reputation-based controls and static analysis frequently allow the initial interaction to pass.
For enterprises, this creates a visibility gap at the most critical moment: the first user clicks. By the time suspicious behavior is detected, credentials may already be compromised, and attackers may have established access that leads to broader financial or operational impact.
| Expose cloud-hosted phishing through real execution before “trusted” infrastructure turns into a business compromise. Access ANY.RUN now. |
What the Investigation Revealed Inside an Interactive Sandbox
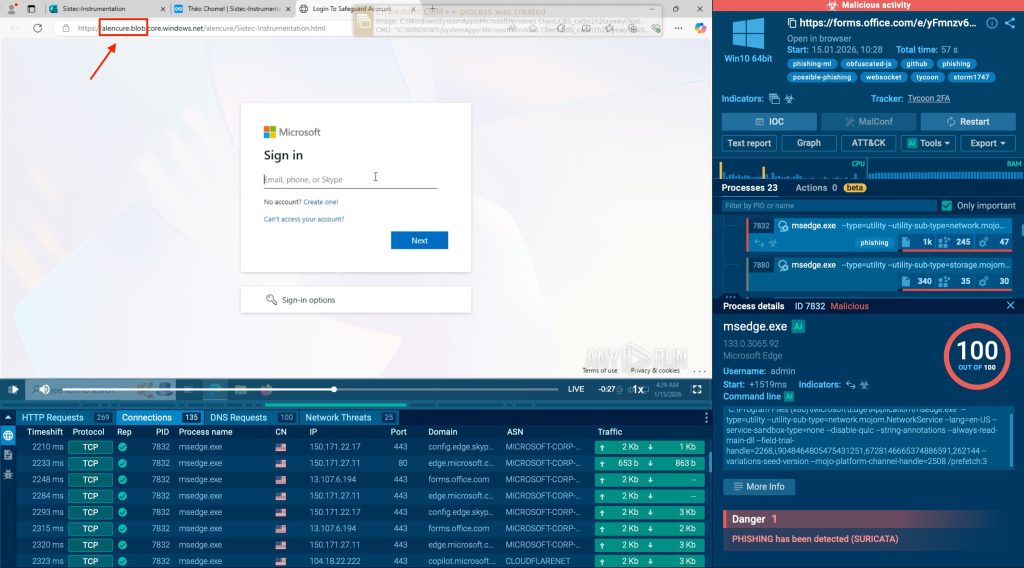
This trend was analyzed inside ANY.RUN’s interactive sandbox because uncovering this type of phishing reliably requires behavioral execution and network-level visibility. In many of these cases, the hosting domains themselves are flagged as legitimate by security tools, since they belong to widely trusted cloud and CDN providers.
Only by executing the attack flow end to end does the malicious intent become clear.
During sandbox analysis, the following sequence was observed:
Step 1: Phishing Loads from Trusted Cloud/CDN Infrastructure
The campaign is hosted on legitimate platforms (not newly registered domains). The tweet lists examples hosted on trusted provider domains, including Azure Blob Storage, Firebase Storage, AWS CloudFront, and Google Sites.
Step 2: The Page Looks “Clean” at First Glance
At first glance, the URL looks safe because it belongs to a well-known provider domain. From the network side, the initial activity can resemble ordinary web content loading from cloud infrastructure.
Step 3: Enterprise Targeting Shows Up in Specific Campaigns
In some observed cases, the phishing flow filters out free email domains and focuses on corporate accounts via a fake Microsoft 365 login experience; a tactic intended to narrow targeting to enterprise users.
Step 4: Runtime Behaviour Exposes What Static Signals Miss
What appears legitimate initially is exposed through sandbox execution. In ANY.RUN Sandbox, the malicious flow becomes visible quickly in under 60 seconds, helping reduce time to detection and response.
How Cloud-Hosted Phishing is Exposed Through Sandbox Analysis
Cloud-hosted phishing is designed to delay clarity. When domains look legitimate, and content appears harmless, analysts lose time trying to confirm intent. Interactive sandbox analysis shortens that gap by turning uncertain alerts into observable behavior.
Inside ANY.RUN’s sandbox, these campaigns are exposed through execution, not assumptions.
Key advantages analysts gain during investigation:
- Full attack chain visibility in less than a minute: Redirects, gated pages, fake login flows, and credential-harvesting logic become visible as the attack unfolds, instead of being pieced together manually.
- Behaviour-first verdicts instead of reputation guesswork: Even when domains belong to trusted cloud providers, malicious intent is confirmed through real runtime actions and network behaviour.
- Automated Interactivity to maintain attack flow: The sandbox automatically interacts with pages by following redirects, solving CAPTCHA challenges, and opening hidden or embedded content. This keeps phishing chains moving and mirrors real user behavior.
- AI-assisted analysis and context: Observed behaviour is summarized and explained to help analysts quickly understand what’s happening, reducing manual interpretation time.
- Auto-generated reports for faster handoff: Network activity, behaviour timelines, and extracted indicators are compiled into a ready-to-use report, supporting faster escalation and response.
For analysts, this approach removes uncertainty. Instead of debating whether a trusted cloud link is dangerous, sandbox execution provides concrete evidence, allowing teams to act faster, reduce investigation time, and prevent cloud-hosted phishing from turning into a business-impacting incident.
Validate Cloud-Hosted Phishing Before It Hits the Business
SOC teams using interactive sandbox analysis report measurable operational gains when cloud-hosted phishing is validated through execution instead of reputation checks.
Across real-world workflows, teams have seen:
- 21 minutes cut from MTTR per case, by confirming malicious behavior early
- Up to 94% faster triage, as analysts start with execution evidence instead of assumptions
- Up to 20% lower Tier 1 workload, by removing ambiguity at the first decision point
- Around 30% fewer Tier 1 → Tier 2 escalations, thanks to clearer verdicts and stronger confidence
Access ANY.RUN’s sandbox to validate complex phishing and malware attacks through real execution, capture the full chain in minutes, and produce escalation-ready evidence with less manual work.
(Image by JetalProduções from Pixabay)