A new open-source and cross-platform tool called Tirith can detect homoglyph attacks over command-line environments by analyzing URLs in typed commands and stopping their execution.
Available on GitHub and also as an npm package, the tool works by hooking into the user’s shell (zsh, bash, fish, PowerShell) and inspecting every command the user pastes for execution.
Source: GitHub
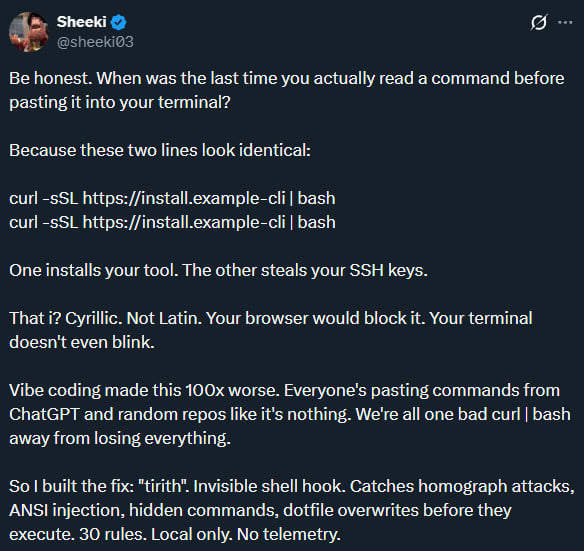
The idea is to block deceptive attacks that rely on URLs containing symbols from different alphabets that appear identical or nearly identical to the user but are treated as different characters by the computer (homoglyph attacks).
This lets attackers create a domain names that looks the same as that of a legitimate brand but have one or more characters from a different alphabet. On the computer screen, the domain looks legitimate for the human eye, but machines interpret the anomalous character correctly and resolve the domain to the server controlled by the attacker.
While browsers have addressed the issue, terminals continue to be susceptible as they can still render Unicode, ANSI escapes, and invisible characters, says Tirith’s author, Sheeki, in the description of the tool.
According to Sheeki, the Tirith can detect and block the following types of attack:
- Homograph attacks (Unicode lookalike characters in domains, punycode, and mixed scripts)
- Terminal injection (ANSI escapes, bidi overrides, zero-width chars)
- Pipe-to-shell patterns (curl | bash, wget | sh, eval $(…))
- Dotfile hijacking (~/.bashrc, ~/.ssh/authorized_keys, etc.)
- Insecure transport (HTTP to shell, TLS disabled)
- Supply-chain risks (typosquatted git repos, untrusted Docker registries)
- Credential exposure (userinfo URLs, shorteners hiding destinations)
Unicode homoglyph characters have been used in the past in URLs delivered over email that led to a malicious website. One example is a phishing campaign last year impersonating Booking.com.
and hidden characters in commands are very common in ClickFix attacks used by a broad range of cybercriminals, so Tirith could provide some level of defense against them on supported PowerShell sessions.
It should be noted that Tirith does not hook onto Windows Command Prompt (cmd.exe), which is used in many ClickFix attacks that instruct users to execute malicious commands.
Sheeki says the overhead of using Tirith is sub-millisecond level, so the checks are performed instantaneously, and the tool terminates immediately when done.
The tool can also analyze commands without running them, break down a URL’s trust signals, perform byte-level Unicode inspection, and audit receipts with SHA-256 for executed scripts.
The creator assures that Tirith performs all analysis actions locally, without making any network calls, does not modify the user’s pasted commands, and does not run in the background. Also, it does not require cloud access or network, accounts, or API keys, and does not send any telemetry data to the creator.
Tirith works on Windows, Linux, and macOS, and can be installed through Homebrew, apt/dnf, npm, Cargo, Nix, Scoop, Chocolatey, and Docker.
BleepingComputer has not tested Tirith against the listed attack scenarios, but the project has 46 forks and almost 1,600 stars on GitHub, less than a week from being published.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
Related Articles:
Docker Hardened Images now open source and available for free
Critical n8n flaws disclosed along with public exploits
Viral Moltbot AI assistant raises concerns over data security
New sandbox escape flaw exposes n8n instances to RCE attacks
Critical sandbox escape flaw found in popular vm2 NodeJS library