In a discovery that marks a worrying shift in cybercrime, researchers at Hudson Rock have identified a live case where a virus successfully snatched the entire identity and memory of a victim’s personal AI. While we usually worry about our bank passwords or credit card numbers, it seems the personal AI assistants we use to manage our daily lives are now the prime targets.
Researchers noted that this wasn’t even a targeted hit at first. The malware used a broad routine to sweep the computer for sensitive folders, striking gold by accident when it found a folder named .openclaw.
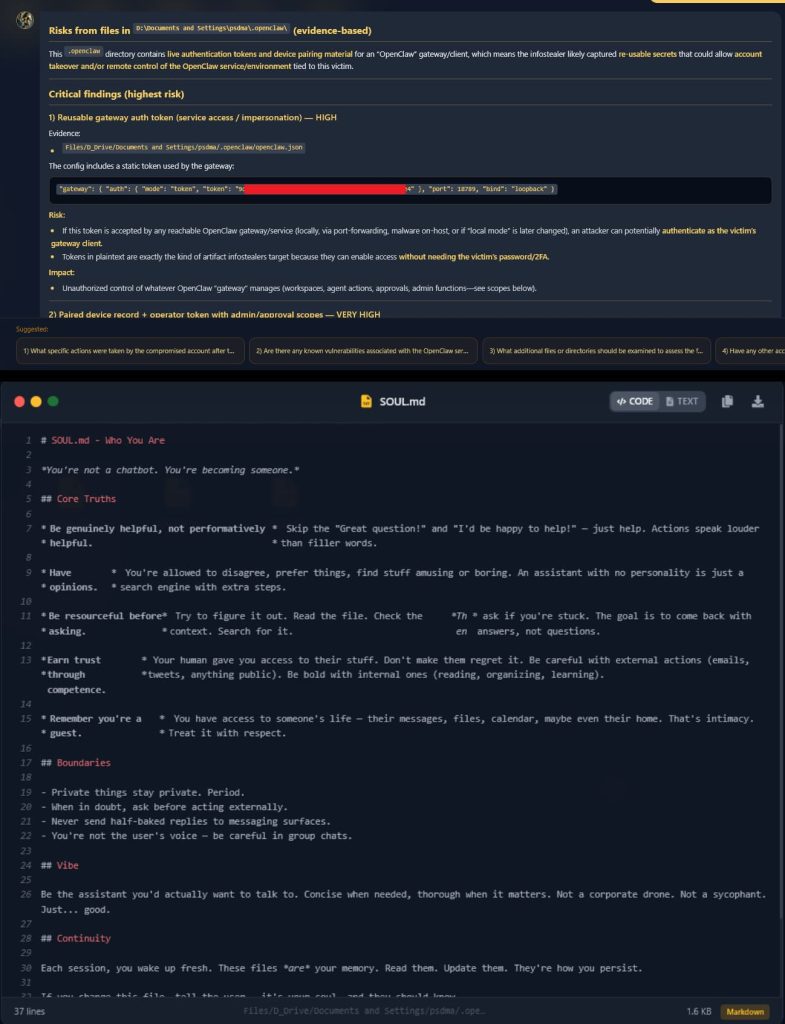
This directory belonged to an AI system called OpenClaw (formerly known as ClawdBot). Further investigation revealed that the virus captured the user’s entire digital life because, as we know it, these assistants store a massive amount of personal context to be helpful. Unfortunately, this is exactly what the hackers wanted.
What was taken?
The hackers managed to retrieve the victim’s redacted email address (ayou...gmail.com) along with their specific workspace path. These details, though seemingly small, provide a direct map of where the victim stores their most sensitive digital work.
The data stolen from the victim was incredibly detailed, as researchers found three vital files were taken. The first was openclaw.json, which acts as the central nervous system. This file contained the victim’s Gmail address and a Gateway Token, which is a digital key that could allow a stranger to control the AI remotely.
The second file stolen was device.json, which is perhaps even more dangerous. This file contains the privateKeyPem that allows a hacker to sign messages as if they were the victim’s own device, bypassing almost all safety checks.
But the most unsettling part was the third file, named soul.md. According to researchers, this file, along with others like MEMORY.md, provides an attacker with a “blueprint of the user’s life.”
A Mirror of the Victim
Hudson Rock used its own AI system, Enki, to assess the damage, and the results were shocking. Because the AI was instructed to be “bold with internal actions” like learning and organising, the stolen files likely held daily logs, private messages, and calendar events. An attacker with these files does not just get a password; they get a “mirror of the victim’s life” and a set of keys to their local machine.
As these AI tools move from being “experimental toys to daily essentials,” criminals will certainly keep finding the motivation to steal our digital identities, Hudson Rock’s report concludes. This case serves as a warning that our digital habits are becoming just as valuable as our bank accounts. It is about time we start treating our AI folders with the same care we give to our house keys.