ESET researchers have identified an Android malware implant that uses generative AI (GenAI) for persistence purposes.
This malicious implant is an advanced version of VNCSpy, a piece of malware that appeared on VirusTotal in January 2026 and was represented by three samples uploaded from Hong Kong.
VCNSpy is an Android malware implant that deploys a virtual network computing (VNC) module on the victim's device, allowing attackers to see the screen and perform actions remotely.
VNC modules are components of screen-sharing technology that enables remote control of another computer using the remote frame buffer (RFB) protocol.
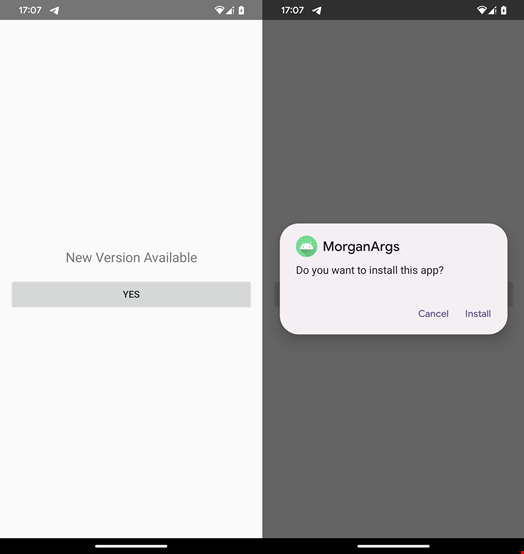
In February, ESET researchers identified four new malware samples uploaded to VirusTotal from Argentina. Their analysis revealed multistage malware based on VNCSpy but with a malicious payload that leverages Google’s Gemini to analyze the targeted device’s screen and provide the operator with step-by-step instructions on how to ensure the malicious app remains pinned in the recent apps list, thus preventing it from being easily swiped away or killed by the system.
The researchers have named the malware implant PromptSpy.
Based on the presence of Simplified Chinese elements in the code, ESET assessed “with medium confidence” that PromptSpy was developed in a Chinese‑speaking environment.
While the security firm noted it hasn’t yet seen any samples of PromptSpy in its telemetry, the existence of a possible distribution domain could suggest the malware has been deployed in the wild.
Malicious App Impersonating JPMorgan Argentina
The four PromptSpy dropper samples were distributed through the website mgardownload[.]com, which was already offline during ESET’s analysis.
After installing and launching PromptSpy dropper, it opened a webpage hosted on m‑mgarg[.]com.
“Although this domain was also offline, Google’s cached version revealed that it likely impersonated a Chase Bank (legally, JPMorgan Chase Bank N.A.),” wrote the ESET researchers in a report published on February 19.
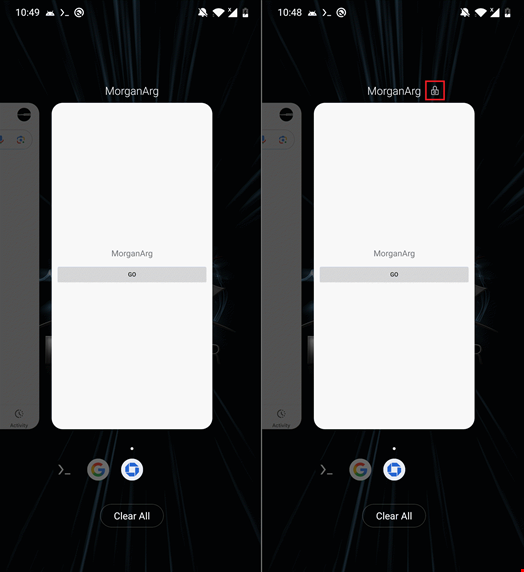
Additionally, the malicious Android app distributing PromptSpy is called ‘MorganArg,’ which suggests it purports to be ‘Morgan Argentina.’ The app’s icon is inspired by Chase bank.
The malicious app is linked to a spoofed Spanish website, with an “Iniciar session” (Login) button, indicating that the page was probably intended to mimic a bank website.
The MorganArg app is a trojan that functions as a companion application developed by the same threat actor behind VNCSpy and PromptSpy.
In the background, the trojan contacts its server to request a configuration file, which includes a link to download another Android package kit (APK) – the file format for Android applications – presented to the victim, in Spanish, as an update.
The configuration server was no longer accessible during ESET’s analysis, so the exact download URL remains unknown.
“However, given that it uses the same unique bank spoofing website, the same app name, icon, and, most importantly, is signed by the same unique developer certificate as the PromptSpy dropper, we strongly suspect this app may serve as the initial stage designed to lead victims toward installing PromptSpy.
Both VNCSpy and PromptSpy include a VNC component, giving their operators full remote access to compromised devices once victims enable Accessibility Services.
This allows the malware operators to see everything happening on the device and to perform taps, swipes, gestures and text input as though they were physically holding the phone.
Gemini AI Helps Maintaining Persistence
PromptSpy also integrates an AI‑assisted user interface (UI) manipulation feature, helping it maintain persistence by keeping the malicious app pinned in the recent apps list
“We believe this functionality is used before the VNC session is established, so that the user or system will not kill the PromptSpy activity from the list of recent apps,” the ESET researchers wrote.
The researchers explained that Android malware usually depends on hardcoded screen features such as taps, coordinates, or UI selectors and that these methods are dependent on UI changes across devices, OS versions or manufacturer skins.
PromptSpy’s Gemini-powered feature aims to achieve persistence by staying embedded in the list of recent apps by executing the “lock app in recent apps” gesture, which varies between devices and manufacturers. This makes it difficult to automate with fixed scripts traditionally used by Android malware.
Once installed and launched, PromptSpy requests ‘Accessibility Service’ permissions, giving the malware the ability to read on‑screen content and perform automated clicks.
Then, while showing a simple loading-style decoy screen in the foreground. The malware begins communicating with Gemini AI to obtain instructions needed to lock its process in the ‘Recent Apps’ list.
When the user sees the ‘Loading, please wait’ activity, PromptSpy uses Accessibility Services to open the ‘Recent Apps’ screen and collect detailed UI information: visible text, content descriptions, class names, package names and screen bounds.
It serializes this dynamic UI snapshot as XML and includes it in its prompt to Gemini. Gemini then returns step-by-step tap instructions on how to achieve the ‘app lock’ gesture.
This process forms a continuous loop:
- PromptSpy sends updated UI context to Gemini
- Gemini replies with new actions
- PromptSpy executes them and returns the resulting screen state
The loop continues until Gemini confirms that the app is successfully locked in recent apps.
All actions suggested by Gemini (taps, swipes, navigation) are executed through ‘Accessibility Services,’ allowing the malware to interact with the device without user input.
The malware communicates with its hardcoded command‑and‑control (C2) server at 54.67.2[.]84 using the VNC protocol. The messages are AES-encrypted using a hardcoded key.
Through this communication channel, the malware can:
- Receive a Gemini API key
- Upload the list of installed apps
- Intercept the lockscreen PIN or password
- Capture the pattern unlock screen as a recording video
- Report whether the screen is on or off
- Report the current foreground app
- Record the screen and user gestures for apps specified by the server
- Take screenshots on demand
PromptSpy blocks uninstallation by overlaying invisible elements on the screen, meaning the only way for a victim to remove it is to reboot the device into ‘Safe Mode,’ where third‑party apps are disabled and can be uninstalled normally.
“PromptSpy shows that Android malware is beginning to evolve in a sinister way. By relying on generative AI to interpret on‑screen elements and decide how to interact with them, the malware can adapt to virtually any device, screen size, or UI layout it encounters,” the ESET researchers concluded.