A new scam is making the rounds online, and it is catching people off guard by mimicking a tool we all use: the CAPTCHA. We have all seen those boxes asking us to prove we are not robots. However, threat hunting experts at CyberProof have found that hackers are now using fake versions of these checks to trick users into infecting their own computers.
Most users, as we know it, trust these verification steps, which is exactly what the attackers are counting on. This research, shared with Hackread.com, indicates the campaign is an evolved version of the ClickFix attacks that targeted restaurant bookings in early 2025.
A Sneaky Multi-Stage Infection
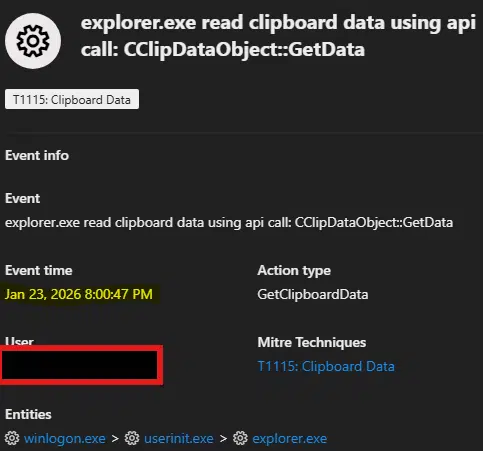
For your information, this attack does not happen all at once. It starts when a person lands on a compromised website and is asked to complete a fake captcha. On 23 January 2026, analysts noticed something odd: the site tried to trigger a command on the user’s machine to read clipboard data using a function called CClipDataObject::GetData.
Further investigation revealed that once the victim interacts with the page, a built-in Windows tool called PowerShell is triggered. This reaches out to a hacker-controlled address, specifically 91.92.240.219, to download the virus.
Researchers also found that the hackers use software called Donut to hide their tracks. This creates a file named cptch.bin, known as shellcode. According to their analysis, this allows the malware to hide directly in the computer’s memory using commands like VirtualAlloc and CreateThread, making it nearly invisible to standard security scans that only look at files on the hard drive.
What are they stealing?
The goal here is simple- total data theft. This infostealer is programmed to be very picky, first checking if it is running on a real computer or a virtual environment used by experts to catch hackers. Once it feels safe, it starts raiding the system.
CyberProof’s blog post reveals that the malware targets cryptocurrency wallets such as MetaMask, Exodus, and Trust Wallet. It also steals saved logins from over 25 browsers, including Chrome, Edge, Opera GX, and the privacy-focused Tor Browser. In addition, it hunts for Steam accounts, VPN settings like NordVPN, and even FTP details used for website management.
The attackers did make a clumsy mistake, though. Researchers noted they used the variable name “$finalPayload”, which acted like a red flag for Microsoft Defender, which flagged it as Behavior:Win32/SuspClickFix.C. However, the hackers remain persistent, hosting various versions like cptchbuild.bin across addresses, including 94.154.35.115 and 178.16.53.70.
It is worth noting that a public report by R.D. Tarun on 1 February 2026 also spotted these same addresses. To keep the virus active, attackers even tweak the RunMRU registry keys so the infection restarts every time you boot up. The key takeaway here is that even the most familiar security checks can be turned against us if we aren’t careful about where we click.